Cisco Firewall Design and Deployment
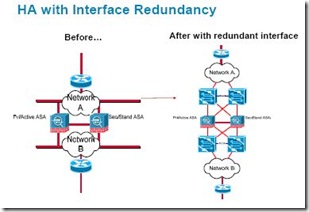
The session about firewall design and deployment didn’t reveal a lot of new things about the Cisco ASA appliance or FWSM module. The only new thing for me was the possibility to configure a redundant interface for a Cisco ASA appliance. The screen shot below shows the cabling scheme for an implementation with and without interface redundancy.
This interface redundancy makes it possible to connect a ASA to two different physical switches. When the active switch would crash, the second switch would become the active switch.
Important here is to notice that this configuration doesn’t provide load-balancing across two links. The configuration is only for link redundancy.
To configure interface redundancy you can use the configuration snippet shown below.
interface Redundant1
member-interface GigabitEthernet0/2
member-interface GigabitEthernet0/1
no nameif
no security-levelno ip address
!
interface Redundant1.4
vlan 4
nameif inside
security-level 100
ip address 172.16.10.1 255.255.255.0
!
interface Redundant1.10vlan 10
nameif outside
security-level 0
ip address 172.16.50.10 255.255.255.0
The configuration of interface redundancy has some caveats as listed below:
- Firewalls have to be configured in Active/Standby mode. No load-balancing or link aggregation is supported;
- Interface redundancy is available on Cisco ASA 5510 and above. The ASA 5505 already has a build in switch and FWSM doesn’t have any physical interfaces;
- Subinterfaces (IEEE 802.1Q) need to be configured on top of the logic redundant interface;
During the session the different modes for the firewalls have been discussed. Normally we only use the Routed Mode, but there are more modes like described below:
- Routed mode: traditional mode of the firewall. Two or more interfaces that separate two or more layer 3 domains;
- Transparent mode: the firewall acts as a bridge and functions mostly at layer 2 of the OSI model (this functions is often used for filtering traffic between two routers who, for example, exchange routing information through a dynamic routing protocol);
- Multi-context: one physical firewall is divided in more virtual firewalls;
- Mixed mode: using routed and transparent firewalls in a virtual environment (NOTE: mixed mode is only supported in FWSM today);
Firewall virtualization using multiple context has some caveats. We, Ictivity consultants, already noticed these caveats during firewall implementations. Firewall virtualization has the following caveats:
- No support for VPN services;
- No support for dynamic routing protocols;
- No way to configure the sharing of CPU usage between contexts;
- No support for multicast routing (multicast bridging is supported);
Especially not supporting VPN services (site-to-site VPN, remote access VPN and SSL VPN) is mostly the most used reason for not using multiple context implementation for the firewall.
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021