Aruba Networks, ClearPass, Configuration Example, Security, Switching
Downloadable User-Roles and NTP sync
The HPE Aruba switches have this cool feature called downloadable user-roles (DUR). DUR enables the switch to use a central ClearPass server to download user-roles to the switch for authenticated users.
More and more customers want to implement wired authentication to strengthen the security level of their network. Via DUR the switches perform an HTTPS API request against ClearPass to download the user-role configuration. This makes the configuration of multiple switches easier, because you don’t need to configure the user-roles locally on the switches anymore, but you push them from a central server. The communication between switch and ClearPass is illustrated in the picture below.
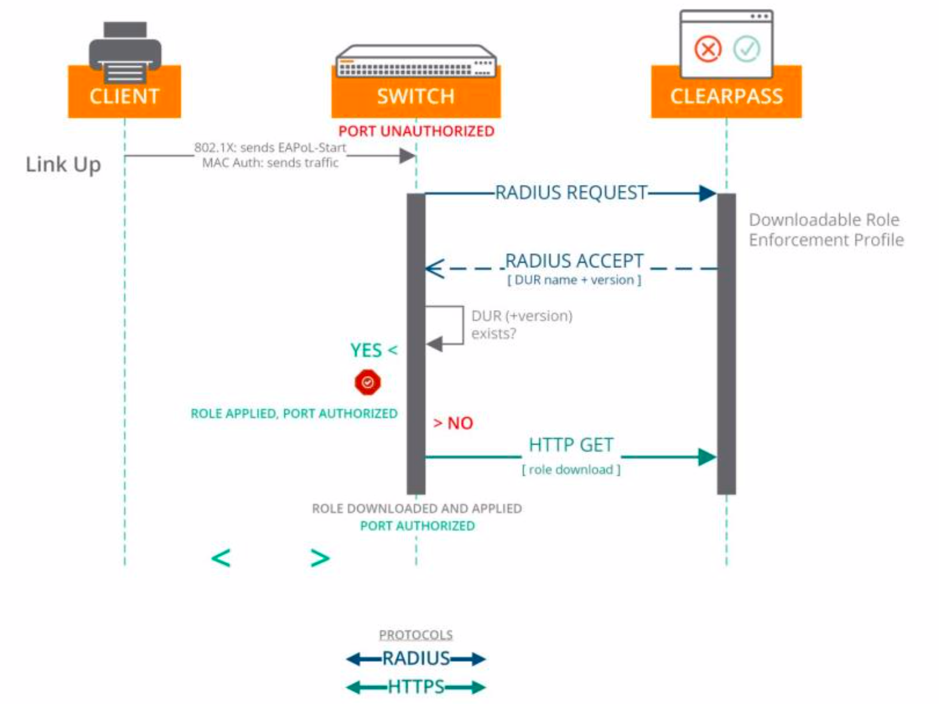
I won’t describe the whole DUR configuration step-by-step, but below you can find the most important configuration for the switch.
radius-server host “cp01.booches.nl” key “radius-secret”
radius-server host “cp01.booches.nl”dyn -authorization
radius-server host “cp01.booches.nl” time-window plus-or-minus-time-window
radius-server host “cp01.booches.nl” time-window 30
radius-server host “cp01.booches.nl”clearpass
radius-servercppm identity “admdur ” key “admdur -key”
!ip client-tracker trusted
!
aaa server-group radius “GRP-CPPM” host “cp01.booches.nl”
!
aaa authentication port-accesseap -radius server-group “GRP-CPPM”
aaa authentication mac-based chap-radius server-group “GRP-CPPM”
aaa accounting network start-stop radius server-group “GRP-CPPM”
aaa authentication captive-portal enable
aaa authorization user-role enable download
!
aaa port-access authenticator 1/1
aaa port-access authenticator 1/1 tx-period 10
aaa port-access authenticator 1/1 supplicant-timeout 10
aaa port-access authenticator 1/1 client-limit 10
aaa port-access mac-based 1/1
aaa port-access mac-based 1/1addr -limit 10
aaa port-access 1/1 controlled-direction in
For the HTTP GET to work the switch needs to trust the certificate chain from ClearPass. In ArubaOS 16.08 and later the certificate is automatically downloaded when specifying the option “clearpass” when configuring the RADIUS client. Another very important step for DUR to work is NTP time sync. The time on the switches needs to be in sync and here a “problem” arises.
After a switch power outage, the switch has to sync its time with an NTP server. And the time needs to be in sync before the first wired clients start authenticating. Even when I use the “
Below you see the output from “show log -r” when the client authenticates, but the switch hasn’t synced its time yet.
I 02/12/19 10:55:46 04908
ntp : ST1-CMDR: The system clock time was changed by 918813141 sec 661757827nsec . The new time is Tue Feb 12 10:55:46 2019
I 01/01/90 01:03:11 04911ntp : ST1-CMDR: The NTP Server 10.10.1.1 is unreachable.
I 01/01/90 01:02:55 00584 WebMacAuth: ST1-CMDR: Port 1/1, re-auth timeout 10 too short.
I 01/01/90 01:02:55 05747 DFP: ST1-CMDR: device_fingerPrinting: Hardware Rules updated successfully for port:1/1, protocol:80, client:08:00:0F:9D:45:BF
W 01/01/90 01:02:55 05204 dca: ST1-CMDR: Failed to apply user role VOIP___DUR-3005-1_7Z4q to macAuth client 08000F9D45BF on port 1/1: user role is invalid.
W 01/01/90 01:02:55 05620 dca: ST1-CMDR: macAuth client 08000F9D45BF on port 1/1 assigned to initial role as downloading failed for user role VOIP___DUR-3005-1.
I 01/01/90 01:02:51 00076 ports: ST1-CMDR: port 1/1 is nowon-line
I 01/01/90 01:02:51 00435 ports: ST1-CMDR: port 1/1 is Blocked by STP
The port is placed in the initial-role which is by default the role
User Role Information
Name : denyall
Type : predefined
Reauthentication Period (seconds) : 0
Cached Reauth Period (seconds) : 0
Logoff Period (seconds) : 300
To “fix” this issue I added a new local user-role to the switch and configured this user-role as initial-role. I added the reauthentication period to the user-role, so the clients reauthenticate when time isn’t synced yet and they receive this initial-role from the switch. The configuration of the role is displayed below.
class ipv4 “IP_ANY_ANY”
10 match ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
exit
policy user “DENYALL”
10 class ipv4 “IP_ANY_ANY” action deny
exit
aaa authorization user-role name “reauth-role”
policy “DENYALL”
reauth-period 30
vlan-id 1
exit
To use this role as initial-role you need to execute the following command.
aaa authorization user-role initial-role reauth-role
=============================================
Edited: February 13th 2019
I created a topic on the AirHeads community on this matter and HPE Aruba responded with:
A software fix for the clock reset on cold boot/power loss issue on the 2930F and 2540 is in the works, and is expected to be released by the end of February.
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021
Hi Rene,
Thank you for your post. I was able to configure a 3810 switch to download user role from the Clearpass. I’m trying to do the same thing with S3500 but getting the following errors
Aug 17 08:39:30 :199802: |authmgr| Old Role: Printer-3045-12 found but wrong version:12 to current:12
Aug 17 08:39:30 :124004: |authmgr| Role:Printer-3045-12 does not have older version
Aug 17 08:39:30 :124004: |authmgr| Enqueued MAC:40:b0:34:a2:17:36 to role:Printer-3045-12, total:1
Aug 17 08:39:30 :124004: |authmgr| Checking reference count for role:Printer-3045-12
Aug 17 08:39:30 :199802: |authmgr| Role:Printer-3045-12 processing stopped due to whitelist violation
Aug 17 08:39:30 :124004: |authmgr| Role:Printer-3045-12 is now locked from modifications
Aug 17 08:39:30 :199802: |authmgr| remains in previous role. Downloaded Role: Printer-3045-12 is in unrecoverable failure state.
Aug 17 08:39:30 :124004: |authmgr| Checking reference count for role:Printer-3045-12
Would you be able to help me with this?
Hi, many thnaks for the article.
I have a similar config except i want my initialrole to be an alllow all. he clearpass service that is used runs in monitor mode so never pases back a DUR, the theory being that we can look at device fingerprinting and check that a DUR would place it into the correct vlan.
I am constantly getting user role invalid messages for my individual ports. What I have is
class ipv4 “DNS”
10 match udp 0.0.0.0 255.255.255.255 192.168.1.152 0.0.0.0 eq 53
20 match udp 0.0.0.0 255.255.255.255 192.168.2.4 0.0.0.0 eq 53
30 match udp 0.0.0.0 255.255.255.255 192.168.1.88 0.0.0.0 eq 53
exit
class ipv4 “all”
10 match ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
exit
class ipv4 “DHCP”
10 match udp 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255 eq 67
exit
class ipv4 “ICMP”
10 match icmp 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
exit
class ipv4 “Permit-All”
10 match ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
exit
policy user “AllowAll”
10 class ipv4 “DHCP” action permit
20 class ipv4 “DNS” action permit
30 class ipv4 “ICMP” action permit
40 class ipv4 “Permit-All” action permit
exit
aaa authorization user-role name “initial-role”
policy “AllowAll”
exit
aaa authorization user-role name “mydevices”
policy “AllowAll”
vlan-name “mydevices”
exit
aaa authorization user-role enable download
aaa authorization user-role initial-role “initial-role”
aaa port-access 2 controlled-direction in
aaa port-access 2 auth-order authenticator mac-based
aaa port-access 2 auth-priority authenticator mac-based
aaa port-access 2 critical-auth user-role “mydevices”
aaa port-access 2 initial-role “initial-role”
I seem to have 3 problems,
1). a reboot clears the policy statement
2). constantly get
W 07/16/23 07:03:33 05204 dca: Failed to apply user role to macAuth client
D452EE0717F2 on port x: user role is invalid.
messages ( although possibly removing the initial role statement from the port config may have cured this)
3). There seems to be an interaction between. defice fingerprinting on the switch and. having a reauth statement in the role definition. If you have a reauth statement fingerprinting doesnt work, remove the reauth and it does
This is on a 2930 WC.16.11.12
Rgds
Alex