ClearPass, Management, Security
ClearPass, Azure AD, SSO and Object ID
Single sign-on is nothing new and I am not going to tell you how to configure ClearPass to use SAML SSO with Azure AD. There is a lot of documentation available, like:
This post is about an issue I was facing with the role mappings in ClearPass and the groups claim from Azure AD. “Normally” the Object ID’s from all groups are returned from Azure AD to ClearPass.
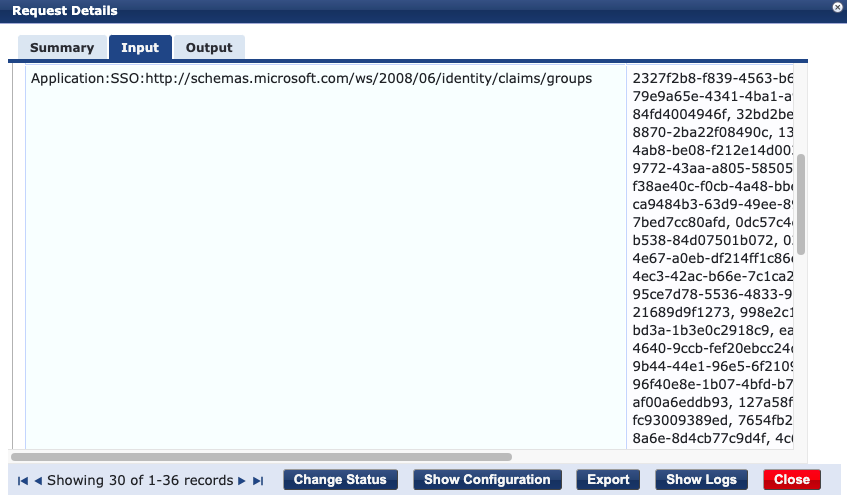
I am using the Object ID’s in the role mappings to assign different CPPM roles to the users. One of my colleagues suddenly complained that he wasn’t able to login to CPPM. I check the Access Tracker and noticed that I was missing the groups information. He didn’t match any role mapping and ended up with a [Deny Application Access Profile].
I did notice a different SSO schema in the Computed Attributes: “Application:SSO:http://schemas.microsoft.com/claims/groups.link”. So instead of the group Object ID’s CPPM received a link to get / view all groups the user is member of. I asked my colleague if something changed with his account. He told me that he joined a lot of project Teams. Every Teams is group he joined in the backend, so he is member of a lot of groups.
I checked the SAML Token Claim Reference documentation and found this note under the Groups claim.
If the number of groups the user is in goes over a limit (150 for SAML, 200 for JWT) then an overage claim will be added the claim sources pointing at the Graph endpoint containing the list of groups for the user.
I unsuccessfully checked the Microsoft documentation if there is a way to change these values. Luckily there is a way to filter which groups Object ID’s returned in the SAML request. This can be changed by changing the user.groups claim in the Enterprise Application configuration on the Azure portal.
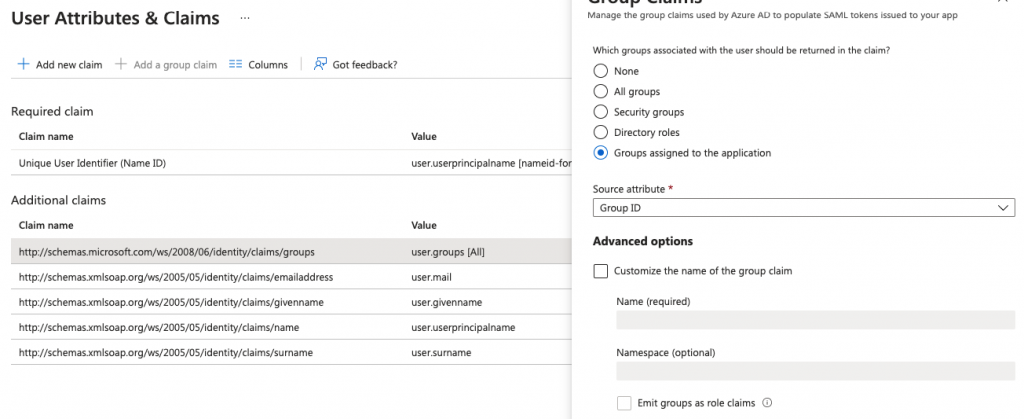
The default value is “All groups”, which returns all group Object ID’s till the maximum is reached. I changed this value to “Groups assigned to the application”. The results in the fact that only the group Object ID’s which are allowed to use this Enterprise Application are returned to CPPM.
This still gives me the opportunity to configure role mappings based on the Object ID and my colleague is able to login again. So everybody is happy!!
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021