Configuration Example, Security
MAC Authentication Bypass – Continued
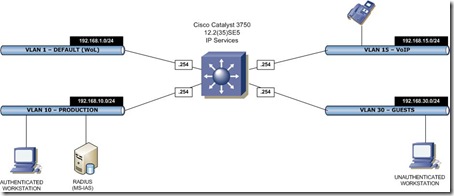
Finally I had a day “off” and could test MAC Authentication Bypass (MAB) in our test environment at the office. I created the following test environment:
There are 4 different VLAN’s and a Cisco Catalyst 3750 connects the VLAN’s to each other. I wanted to create an environment with the following properties:
- All switch ports are default member of VLAN 1;
- Authenticated workstations become member of VLAN 25;
- Unauthenticated workstation become member of VLAN 30;
- VoIP phones are member of VLAN 15;
- All workstation should be able to boot with Wake on LAN;
- MS-IAS is used as RADIUS Authentication server;
I have configured the necessary components and got the environment working with the above properties. The next few sections cover the configuration of the different components.
Cisco Catalyst 3750
Most of the configuration is done on the Cisco Catalyst 3750 switch. First of all I created the different VLAN’s on layer 2 of the OSI model. Next I created the SVI’s to make the VLANs routable. I used the standard SVI configuration. I used the ‘quick-and-dirty’ solution for configuring Wake On LAN (WOL) by just adding the ip directed-broadcast command to the SVI’s. The snippet below shows the SVI configuration.
Interface Vlan1
ip address 192.168.1.254 255.255.255.0
ip directed-broadcast
end
!
Interface Vlan10
ip address 192.168.10.254 255.255.255.0
ip directed-broadcast
end
!
Interface Vlan15
ip address 192.168.15.254 255.255.255.0
end
!
Interface Vlan30
ip address 192.168.30.254 255.255.255.0
end
The next step is configuring AAA and the RADIUS group for authenticating the connected clients to the network. The snippet shows these configuration.
aaa new-model
aaa authentication dot1x default group radius
aaa authorization network default group radius
!
radius-server host 192.168.10.30 auth-port 1812 acct-port 1813 key ictivity
The following step is to enable 802.1x globally in the switch. You should use the command in the following snippet to enable 802.1x.
dot1x system-auth-control
The last configuration snipper shows the configuration of a switch port. This switch port is configured use MAC Authentication Bypass as backup authentication method if 802.1x cannot authenticate.
interface GigabitEthernet1/0/16
switchport mode access
switchport voice vlan 15
dot1x mac-auth-bypass
dot1x pae authenticator
dot1x port-control auto
dot1x control-direction in
dot1x timeout tx-period 1
dot1x max-reauth-req 1
dot1x guest-vlan 30
spanning-tree portfast
spanning-tree bpduguard enable
MS-IAS
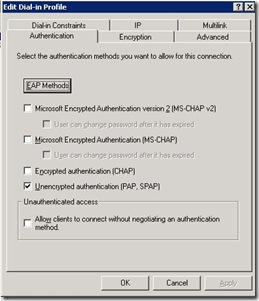
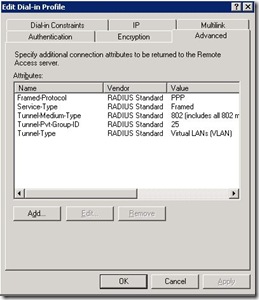
I configured Internet Authentication Services on a Windows 2003 server. I didn’t configure the Active Directory, but use the local users and local groups to authenticate. I configured the RADIUS client inside IAS and started to create a Remote Access Policy. The Remote Access Policy matches a newly created Windows Group. The important aspects of the Policy are the Authentication options and the Advanced Attributes. The configuration of both is shown below.
The last step in the whole process is configuring the Windows Group and adding users to that group. The MAC address of the workstation is acting as username and password. Important to notice is that all characters are case-sensitive and the username and password should only contain lowercase characters. An example of username and password is: 0016762eccda.
After configuring the test environment I have done some testing. First was trying to connect a workstation and authenticate. This is working perfectly, you will see a nice IAS event message on the Windows 2003 server. Next I connected an IP Phone with a build-in switch and connected the workstation to the IP Phone. The workstation again authenticates flawlessly against the RADIUS server. The last test was trying to wake up the workstation via Wake On LAN. When you should down the workstation, the switch ports first goes in shutdown and re-enables after the complete shutdown of the workstation. Next the switch ports returns to Vlan 1 (switchport access vlan 1). I send the Magic Packet to the broadcast address of VLAN 1. The workstation starts booting and authenticates against the RADIUS server.
I can only say, that MAC Authentication Bypass is working perfectly in my TEST environment. Shortly I will try to implement it on the network of one of our customers, because he wants a cheap method for securing his switch ports.
I know, and I told the customer, that MAC authentication isn’t a very powerful tool for security the switch port. Because spoofing a valid MAC address is enough to get access to the network. But MAC authentication is still better, then no authentication at all. And let’s face it, what are the costs: NOTHING!!!
Most companies have a Windows 2003 server where IAS can be installed or you can use FreeRADIUS, so no costs on the OS. I have tried an IP Base and an IP Services IOS on the Cisco Catalyst 3750, both are working perfectly. A switch has minimal an IP Base image, so no additional costs here. The only costs are made during the configuration and testing of the authentication.
Check the latest article about MAB and MDA in an IP Phone environment
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021
Hi just passed by consedince while looking for some articles :) anyway nice blog Will check it out Later on ,hope you accept me as a follower. thanks ^^