Configuration Example, Security
MAB and MDA in an IP Phone environment
I blogged before about the MAC Authentication Bypass (MAB) feature in network environments. MAC Authentication Bypass can be used to secure the wired network by verifying MAC addresses to a central database. By using a radius server, like Microsoft IAS or FreeRadius, you can also redirect verified MAC addresses to a specific VLAN.
Lately I had a new challenge with configuring MAB. These time a single switch port is shared by an IP phone and a workstation. The IP phone is used as a kind of switch. The backend switching network is build on Cisco Catalyst switches. All IP phone traffic is handled by the voice VLAN and all data traffic is handled by the an access VLAN. The IP phones used in this situation are Mitel 5330 phones. These phones support CDP and also LLDP, which is perfect when using a voice VLAN.
The customer would like the MAC addresses of both devices verified against a central database. In this situation I used Microsoft IAS, because the customer is using Microsoft Active Directory as central database. In Active Directory I created an OU structure with an unique OU and security group for every logical group. So I created an OU voice and a security group voice, and I created a group data and an OU data. The MAC addresses of the components need to be added to Active Directory as users. The account name and the password are exactly the same and equal to the MAC address, like 001f22d712ef. I made the account for the IP phone member of the voice group and the account of the workstation member of the data group.
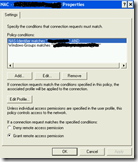
I started with just connecting a single workstation to the switch and configured IAS to verify the MAC address and automatically redirect the workstation to the correct access VLAN. The configuration of IAS is straightforward. First I installed IAS and registered the service in Active Directory. I added the switch as radius client and configured a radius policy for the data connections. The radius policy checks if the MAC address is member of the data group and returns the access VLAN if the MAC address is positively verified. This works without any problems. The screenshots below show the most important configuration of this policy.
Next you see the switch configuration so far.
aaa new-model
!
aaa authentication dot1x default group radius
aaa authorization network default group radius
!
dot1x system-auth-control
!
interface FastEthernet0/35
switchport access vlan 102
switchport mode access
switchport nonegotiate
switchport voice vlan 150
authentication control-direction in
authentication port-control auto
authentication periodic
authentication timer restart 900
authentication timer reauthenticate 5400
mab
spanning-tree portfast
spanning-tree bpduguard enable
end
I configured another policy, exactly the same, for the voice components. I disconnected the workstation and connected the IP phone to the network. This also works without any problems. The IP phone is authenticated and allowed access to the network. Next I connected the workstation to the IP phone and booted the workstation. I noticed that the IP phone lost his power and checked the switch port status. The switch port went in err-disable state with the following message:
Feb 5 08:54:50.095 GMT+1: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface FastEthernet0/35, new MAC address (0080.647f.c590) is seen.
Feb 5 08:54:50.095 GMT+1: %AUTHMGR-5-SECURITY_VIOLATION: Security violation on the interface FastEthernet0/35, new MAC address (0080.647f.c590) is seen.
Feb 5 08:54:50.095 GMT+1: %PM-4-ERR_DISABLE: security-violation error detected on Fa0/35, putting Fa0/35 in err-disable state
This is a big problem, because both network components aren’t able to communicate with the network. I did some research and found the Multiple Domain Authentication (MDA) feature. Multiple Domain Authentication (MDA) allows both a data device and a voice device, such as an IP phone (Cisco or non-Cisco), to authenticate on the same switch port, which is divided into a data domain and a voice domain. This feature is configured with the authentication host-mode commands and is very useful when combining IEEE 802.1x and/or MAB in an IP phone environment. The following host-modes can be used:
Single-host mode should be configured if only one data host is connected. Do not connect a voice device to authenticate on a single-host port. Voice device authorization fails if no voice VLAN is configured on the port.
Multi-domain mode should be configured if data host is connected through an IP Phone to the port. Multi-domain mode should be configured if the voice device needs to be authenticated.
Multi-auth mode should be configured to allow up to eight devices behind a hub to obtain secured port access through individual authentication. Only one voice device can be authenticated in this mode if a voice VLAN is configured.
Multi-host mode also offers port access for multiple hosts behind a hub, but multi-host mode gives unrestricted port access to the devices after the first user gets authenticated.
I tested the multi-host configuration and it did exactly as explained above. Only one device is authenticated and all next device are allowed without authentication. In my situation I have to use multi-domain. I added the configuration line authentication host-mode multi-domain to the interface configuration above. After this I had a new problem. Both devices are authenticated correctly, but the Mitel IP phone got stuck at DHCP Discovery, while the workstation is working correctly.
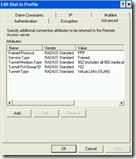
After some sniffing I saw the Mitel phone sending its DHCP Discovery to the data VLAN, but the phone didn’t receive any DHCP Offer from a DHCP server. Back to the drawing table and I found the solution in the radius configuration. I configured the radius attribute cisco-av-pair in order to tell the switch that the IP phone is allowed on the voice VLAN, see the picture.
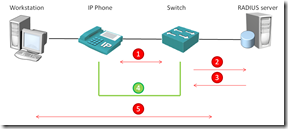 The following steps are taken during the process:
The following steps are taken during the process:
- 1. The IP Phones learns the voice VLAN ID from CDP;
- 2. The switch learns the MAC address of the phone and sends an Accept-Request for the phones MAC address to the radius server;
- 3. The radius server responds with an Access-Accept and adds the Vendor-Specific Attribute (VSA) Cisco-AV-pair with the value device-traffic-class=voice;
- 4. All traffic from the IP Phone is allowed in the voice VLAN and the DHCP process works flawlessly;
- 5. The workstation is also authenticated by the radius server and all data traffic is allowed in the data VLAN;
The radius policy for the voice VLAN is almost equal to the radius policy for the data/access VLAN. The only difference is in the radius attributes. Below you see the attributes for the voice radius policy.
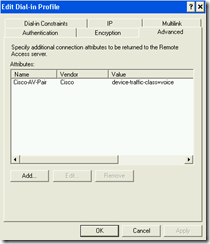 I did some testing and the environment is working perfectly. Both devices are authenticated separately from each other. The final configuration of the switch port looks like this:
I did some testing and the environment is working perfectly. Both devices are authenticated separately from each other. The final configuration of the switch port looks like this:
interface FastEthernet0/35
switchport access vlan 102
switchport mode access
switchport nonegotiate
switchport voice vlan 150
authentication control-direction in
authentication host-mode multi-domain
authentication port-control auto
authentication periodic
authentication timer restart 900
authentication timer reauthenticate 5400
mab
spanning-tree portfast
spanning-tree bpduguard enable
end
Below you see some output from the show authentication sessions command. You can clearly see the domain where the device is authenticated in.
ONLY IP PHONE IS AUTHENTICATED SUCCESSFULLY
switch#show authentication session interface fa 0/35
Interface: FastEthernet0/35
MAC Address: 0800.0f46.874a
IP Address: Unknown
User-Name: 08000f46874a
Status: Authz Success
Domain: VOICE
Oper host mode: multi-domain
Oper control dir: in
Authorized By: Authentication Server
Session timeout: 5400s (local), Remaining: 5397s
Timeout action: Reauthenticate
Idle timeout: N/A
Common Session ID: 0A0A421B00000065C2FF71B0
Acct Session ID: 0x0000014A
Handle: 0x04000065Runnable methods list:
Method State
mab Authc Success
IP PHONE AND WORKSTATION ARE AUTHENTICATED SUCCESSFULLY
switch#show authentication session interface fa 0/35
Interface: FastEthernet0/35
MAC Address: 0080.647f.c590
IP Address: Unknown
User-Name: 0080647fc590
Status: Authz Success
Domain: DATA
Oper host mode: multi-domain
Oper control dir: in
Authorized By: Authentication Server
Vlan Policy: 102
Session timeout: 5400s (local), Remaining: 5364s
Timeout action: Reauthenticate
Idle timeout: N/A
Common Session ID: 0A0A421B00000068C304A7C5
Acct Session ID: 0x0000014D
Handle: 0x56000068Runnable methods list:
Method State
mab Authc Success—————————————-
Interface: FastEthernet0/35
MAC Address: 0800.0f46.874a
IP Address: Unknown
User-Name: 08000f46874a
Status: Authz Success
Domain: VOICE
Oper host mode: multi-domain
Oper control dir: in
Authorized By: Authentication Server
Session timeout: 5400s (local), Remaining: 5340s
Timeout action: Reauthenticate
Idle timeout: N/A
Common Session ID: 0A0A421B00000067C3043675
Acct Session ID: 0x0000014C
Handle: 0xE2000067Runnable methods list:
Method State
mab Authc Success
IP PHONE IS AUTHENTICATED SUCCESSFULLY, WORKSTATION ISN’T
switch#show authentication session interface fa 0/35
Interface: FastEthernet0/35
MAC Address: 0080.647f.c590
IP Address: Unknown
User-Name: UNRESPONSIVE
Status: Authz Failed
Domain: DATA
Oper host mode: multi-domain
Oper control dir: in
Session timeout: N/A
Idle timeout: N/A
Common Session ID: 0A0A421B00000066C300CB6C
Acct Session ID: 0x0000014B
Handle: 0xEB000066Runnable methods list:
Method State
mab Failed over—————————————-
Interface: FastEthernet0/35
MAC Address: 0800.0f46.874a
IP Address: Unknown
User-Name: 08000f46874a
Status: Authz Success
Domain: VOICE
Oper host mode: multi-domain
Oper control dir: in
Authorized By: Authentication Server
Session timeout: 5400s (local), Remaining: 5261s
Timeout action: Reauthenticate
Idle timeout: N/A
Common Session ID: 0A0A421B00000065C2FF71B0
Acct Session ID: 0x0000014A
Handle: 0x04000065Runnable methods list:
Method State
mab Authc Success
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021
Thanks very much for the article, very useful! I’ve been struggling for several hours to set up a similar configuration and with your help I finally got it working.
Thanks for this very helpful article! I have a need to set up something like this… however I have a concern about the security of creating AD users with the username and password the same. Do you have any way of preventing malicious users from abusing those accounts?
My Microsoft colleagues configure some sort of policy which prevents the username / password combination from the logon process into a workstation of other Active Directory computer.
I don’t what they do, but it works. Sometimes they create a dummy Windows group and configure this as primary group for that user. Next they delete the specific user from the Domain Users group, but lately I heard that this method isn’t the preferred method.
Thanks René. There is a setting that you can add to only allow the account to authenticate against particular clients, which I assume would be set to the radius (in my case NPS) server. I will raise this as an option with my colleagues, but I think it is still far from ideal. I am hoping to encourage the powers that be to allocate resourcing to set up a Certificate Authority and do it properly.
dear booche
your document very usefulfor me, but i have a problem when i configuired switch and IAS for dynamic vlan for data and voice and no switchport voice vlan 2 on switch my ipphone can authenticate but no authorize.
please help me.
What do you see in the log and what is the output of the show authentication and show int status command?
on IAS i receive authentication Successful but with status int on switch see this: status is notconnected and switch port on vlan 1 (that vlan 1 is native) .
Notconnected usually indicates that the physical connection isn’t established. Are you sure that the component is physically connected.
thanks for your attention!
yes, IPphone physicaly connected and it has latest ip that receive of DHCP while is on another port that it is not dot1x.
my configuration on swich :
aaa authentication dot1x default group radius
aaa authorization network default group radius
aaa accounting dot1x default start-stop group radius
dot1x system-auth-control
interface FastEthernet0/10
switchport mode access
dot1x mac-auth-bypass
dot1x pae authenticator
dot1x port-control auto
dot1x host-mode multi-domain
dot1x violation-mode protect
spanning-tree portfast
spanning-tree guard root
is it ok ?
I have another question do you know difference between mac-auth-bypass and mac-auth-bypass eap command?
What is the output of the show authentication interface fa0/10 command? What type of IP Phone do you use? When using multi-domain I would recommend configuring a separate Voice VLAN via switchport voice vlan . The multi-domain configuration authenticates the IP phone into the Voice VLAN.
I would also recommend configuring the “control-direction in” feature, so traffic from the switch to the host isn’t authenticated. This allows you to use features like Wake on LAN.
output of show dot1x interface0/10
PAE = AUTHENTICATOR
PortControl = AUTO
ControlDirection = Both
HostMode = MULTI_DOMAIN
Violation Mode = PROTECT
ReAuthentication = Disabled
QuietPeriod = 60
ServerTimeout = 0
SuppTimeout = 30
ReAuthPeriod = 3600 (Locally configured)
ReAuthMax = 2
MaxReq = 2
TxPeriod = 30
RateLimitPeriod = 0
Mac-Auth-Bypass = Enabled
Inactivity Timeout = None
ipphone model: cisco 7911
i want to do dynamic vlan for voice Nevertheless is it necessary switchport voice vlan 2?
i have 3 vlan: 1 native,2 data and 3 voice.
What does the “show authentication interface fastethernet0/10” tell you? That commands shows if an authentication request has been made and the result of that request. You can also see in what domain (data or voice) the clients tries to authenticate.
You can push the correct VLAN ID by using the RADIUS attributes I configured in the example.
i do “show dot1x interface fastethernet0/10 “(my switch ios 12.2(46)se and i should show dot1x no show authentication) and receive:
PAE = AUTHENTICATOR
PortControl = AUTO
ControlDirection = Both
HostMode = MULTI_DOMAIN
Violation Mode = PROTECT
ReAuthentication = Disabled
QuietPeriod = 60
ServerTimeout = 0
SuppTimeout = 30
ReAuthPeriod = 3600 (Locally configured)
ReAuthMax = 2
MaxReq = 2
TxPeriod = 30
RateLimitPeriod = 0
Mac-Auth-Bypass = Enable
nactivity Timeout = None
i check it and client(pc) is in data domain.
i configured radius server from your example.
Sepideh, is it possible to upgrade the IOS on the switch to the latest version? What if you specify the switchport voice vlan command and authenticate the IP Phone into the voice domain.
I haven’t found a way to configure the voice vlan through RADIUS attributes.
dear rene, i can’t upgrade ios . when i specify the switchport voice vlan command IP Phone authenticate into voice domain and there is no problem.
i have found configure the voice vlan through cisco ACS but i dont know IAS how to config.
tanks
dear Rene
Please helpe me, In implementation of MDA and MAB i’ve encountered a new problem.Network card some of PCs randomly for a few minutes go Limited mode after times or restart PC system is ok.
What do you think?
tanks.
oh, I forget to say after this problem i check ias log and i understand that NIC mac come to authentication and users receive authentication failed. I dont khonw what to do!
please help me.
What’s the reason that the mac of the host is denied, when looking at the ias logging.
I want the PC authentication with dot1x no mac and i dont add PC mac address so pc authentication failed.
dear rene
again i check IAS log i have 2 senario for some users in ias user authentication success but port dont up and another case after user authentication success, MAC of NIC come for authentication and ias authentication failed.
Have you tried to configure the authentication order between dot1x and mab?
Below you see the basic configuration to perform both methods on the same interface and using the authentication type PEAP on the authentication server (IAS / NPS):
Interface GigabitEthernet1/0/1
authentication event fail action authorize vlan 1000
authentication order mab dot1x
authentication priority dot1x mab
authentication control-direction in
authentication port-control auto
mab
dot1x pae authenticator
Hi Rene,
Thank you so much for your useful article. I have a question for you I have 2 VLANs :
1- DATA VLAN (VLAN10) and 2- VOICE VLAN (VLAN168)
all the Shoretel IP Phones are in Voice VLAN and DHCP ,Shoretel Switch and Shoretel Server are in VLAN10 not Voice VLAN.
I can authenticate both IP phones and workstations together on dot1x but IP Phones can not get an IP from DHCP. and I do not have any server on IP Phones.
Do you have any suggestion?
Thanks,
Mike
Hey Mike,
The IP phone will send a DHCP request in the Voice VLAN. The request will by default never reach the DHCP server in the data VLAN. To forward the request you need to configure DHCP relay. You can achieve this by configuring DHCP relay (IP helper) on a layer 3 device with a layer 3 interface in both VLAN’s. Another quick-and-dirty solution is by adding an extra NIC to the DHCP server and configure this NIC (including the DHCP scope) in the IP range of the voice VLAN.
I hope this helps to resolve your problem.
René
oh , I forgot that command on the test switch! I will test it and it would be working fine after that. Thanks again for your help
Mike
Hi i’m trying to work with MAB but having problems with creating username (MAC address of phones). If I set the password same as the username, AD (Windows 2003 server) won’t allow me to create username and password which are the same as what MAB is trying to say even though no complex passwords are set. I’m not sure what needs to be done here, hope someone can help! Thanks!
Thank, it work perfectly.
Just a little question, can i make all phone access-accept without MAB ??
Thank again,
PhuocNguyen