Configuration Example, Routing
Policy-based routing in a nutshell
Lately I received some questions about routing decisions and how to influence the routing decisions via access control lists. The following example shows a simple configuration for policy-based routing. The example uses the following logical setup:
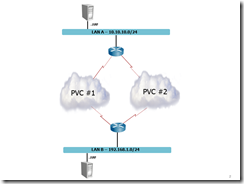 I configured two routers and connected each router to two PVC’s on the same ATM interface. I configured one subnet per location. All normal traffic is router through PVC #1, but all traffic to or from the servers in the picture should be routed to PVC #2.
I configured two routers and connected each router to two PVC’s on the same ATM interface. I configured one subnet per location. All normal traffic is router through PVC #1, but all traffic to or from the servers in the picture should be routed to PVC #2.
The top router has SVI VLAN 1 configured to connected to the inside LAN. The first step in configuring policy-based routing is defining which traffic should be routed over PVC #2. I configured the following access-list.
ip access-list extended acl-pbr
permit ip 10.10.10.0 0.0.0.255 host 192.168.1.100
permit ip host 192.168.1.100 10.10.10.0 0.0.0.255
Next you need to configure a route-map with a “match” statement and configure the appropriate “set” conditions.
route-map rm-pbr permit 10
match ip address acl-pbr
set ip next-hop <PVC #2 IP address>
The last step is applying the configured route-map to the correct interface. As stated before, we are using SVI VLAN 1.
interface Vlan1
ip address 10.10.10.254 255.255.255.0
ip policy route-map rm-pbr
As you can see, configuring policy-based routing is very simple, and yet very powerful.
One issue is when testing policy-based routing from the router. By default, locally-generated packets are not inspected by outgoing access-lists. To enable local packets from being re-entered into the router, you should issue the ip local policy route-map <rm-name>.
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021
Good article thank you.
Do you know how one would route different vlans whos destination was unkown to specific default gateways?
For example:
Cisco L3 switch:
A default gateway already exists (gateway#1) which existing vlans use to get to the internet CPE.
Create new VLANS that would use a new default route (gateway#2) as their gateway of last resort to reach the internet CPE
Both old and new VLANS still need to be able to communicate with each other on the switch
– Any traffic from New vlan 100 to destination unknown/internet go to new gateway #2
– Any traffic from any old VLANs to destination unknown/internet go to new gateway #1
Thank you!