Aruba Networks, ClearPass, Configuration Example, Wireless
ClearPass – concurrent session limit
I tried to configure a restriction to the concurrent number of active sessions a user can have on the wireless network. I found a great article on AirHeads Community “How to deny access for authentication requests based on session limit?”
In short the article tells you to:
- Edit the Insight Repository
- Add more Filiters on the Attributes tab
- Enter the following information
- Filter Name: sessions
- Filter Query: see below
- Name: sessions
- Alias Name: sessions
- Data Type: Integer
- Enabled As: Role
- Add the Insight Repository as Authorization Source
- Create an Enforcement Policy Condition to check the Insight Repository
- Type: Authorization:[Insight Repository]
- Name: sessions
- Operator: GREATER_THAN_OR_EQUALS
- Value: <number of allowed simultaneous connections + 1
I configured my ClearPass environment like shown in the article, but I didn’t see any active sessions in the access tracker. The counter remained 0. I connected to the Insight database with the tool pgAdmin to see if the Insight database is updated. The database is updated, so every thing seems to be working.
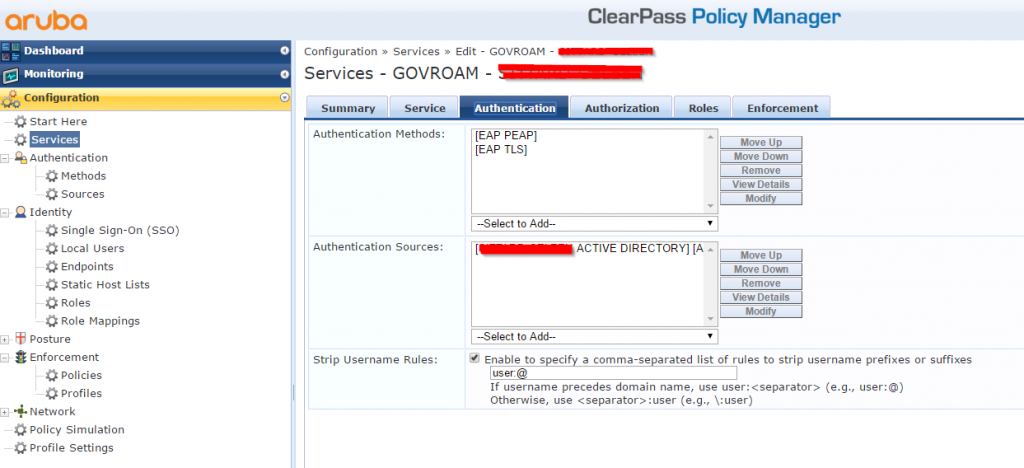
Be accident I found the solution. The SSID is using EAP-PEAP authentication and users enter there username as <username>@<domain-name>, like rene@booches.nl. This is necessary, because the SSID is configured to work with Govroam. Govroam provides government employees with seamless access to WiFi networks, wherever the service has been made available by participating organisations. To authenticated the users correctly, I configured the CPPM Service with Strip Username Rules.
The SQL query checks the attribute %{Authentication:Username}
select count(*) as sessions from radius_acct where (username = ‘%{Authentication:Username}’) AND end_time is null AND termination_cause is null AND (updated_at BETWEEN (now() – interval ‘1 hour’) AND now());
In the InsightDB the username has the format <username>@<domain-name>, but the attribute %{Authentication:Username} has the format <username>. I saw this “mismatch” while checking the Access Tracker.
I altered the query by changing %{Authentication:Username} into %{Authentication:Full-Username}. After this the session information was correct and I could use the session counter in a Role Mapping or Enforcement Profile to limit the concurrent number of active sessions from a user.
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021