Aruba Networks, Cisco, ClearPass
Aruba ClearPass – Cisco Prime – TACACS+
When using Cisco Prime you have the option to configure authentication to a remote AAA server via RADIUS or TACACS+. Today I configured Cisco Prime to use HPE Aruba ClearPass as remote AAA server based on the TACACS+ protocol. The configuration of an AAA server in Cisco Prime is very straightforward. Configure the AAA Mode Setting under Administration / Users / Users, Role & AAA / AAA Mode Settings. The next step involves adding HPE Aruba ClearPass as TACACS+ servers via the option menu Administration / Users / Users, Role & AAA / TACACS+ Servers.
I configured a TACACS+ service in ClearPass with a very basic Enforcement Profile. In the beginning I used the same Enforcement Profile, which I also use to enforce privilege level 15 to switches and routers. Authentication will fail at this point. In the Access Tracker I get the following error message:
Tacacs service=NCS:HTTP not enabled
And the login screen from Cisco Prime shows me the following error message.
I created a new Enforcement Profile and added the TACACS+ service NCS:HTTP to the Enforcement Profile. Now I see an access granted in the Access Tracker, but I still get the same error message on the Cisco Prime website. After some digging in Cisco Prime I noticed that Cisco Prime needs to receive TACACS+ attributes from the AAA server to grant access and assign privileges and tasks to the user.
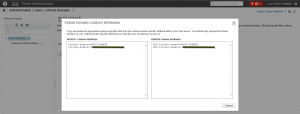
First you need to get the TACACS+ attributes from the Virtual Domain configuration. In the menu options navigate to Administration \ Users \ Virtual Domains. At the upper right corner you have the option to “Export Custom Attributes”.
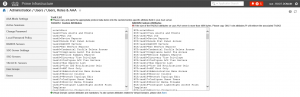
These attributes need to be configured in ClearPass. As you notice you also need to configure these attributes if you would like to use RADIUS as authentication protocol. You also need to add the attributes from the user group. Navigate to Administration / Users / Users, Role & AAA / User Groups. Click the “Task List” option next to the User Group you would like to use. I use Root in this example.
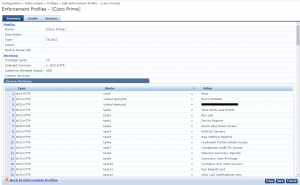
The User Group Root contains 194 tasks, which need to be added to the Enforcement Profile in ClearPass. Below you see a snippet from the Enforcement Profile configuration.
To make it easy for you, I exported the Enforcement Profile including all the 194 tasks for the Root User Group. You can download the Enforcement Profile in XML format below. Just import the profile into ClearPass and you are good to go!!!
Download here: Cisco Prime Enforcement Policy
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021

This is great! Appreciate you providing this breakdown. Absolutely make life easier :)
One question I have – are you able to utilize these same attributes for Cisco Prime LMS as well?
Hello Nicole,
I don’t know for sure, because I haven’t configured a connection between these two. I guess you can, and maybe it is easier to configure RADIUS as authentication method compared to TACACS+
Thanks Rene, very simple steps to follow