Getting your AOS-CX switch in Central
Everybody is talking about Cloud Management and since Aruba Central is upgraded to 2.5.2, there is the ability to manage your AOS-CX switch in Central via Template Groups.
To get this done, it is necessary to get your switch connected to Central and this isn’t always a matter of booting the switch, configure IP address, routing, DNS server and you are ready to go.
After setting up the default settings (and yes the switch has internet access) I see the following message on the switch.
6200F(config)# show aruba-central
Central admin state : enabled
Central location : device-eu-d2.central.arubanetworks.com
VRF for connection : default
Central connection status : connection_failure
Central source : dhcp
Central source connection status : connection_failure
Central source last connected on : N/A
System time synchronized from Activate : False
Activate Server URL : devices-v2.arubanetworks.com
CLI location : N/A
CLI VRF : N/A
The switch doesn’t show up in Central. Some debugging on the switch (“debug central all” with “show debug buffer reverse”) and checking the logging on the switch tells us the following:
2020-11-03T12:17:29.456931+01:00 6200F hpe-restd[1005]: Event|7709|LOG_WARN|UKWN|1|Certificate *.central.arubanetworks.com rejected due to verification failure (30)
So I decided to import the certificate chain from *.central.arubanetworks.com, just like you do for downloadable user-roles in regards to ClearPass. Aruba Central uses the following certificate chain.
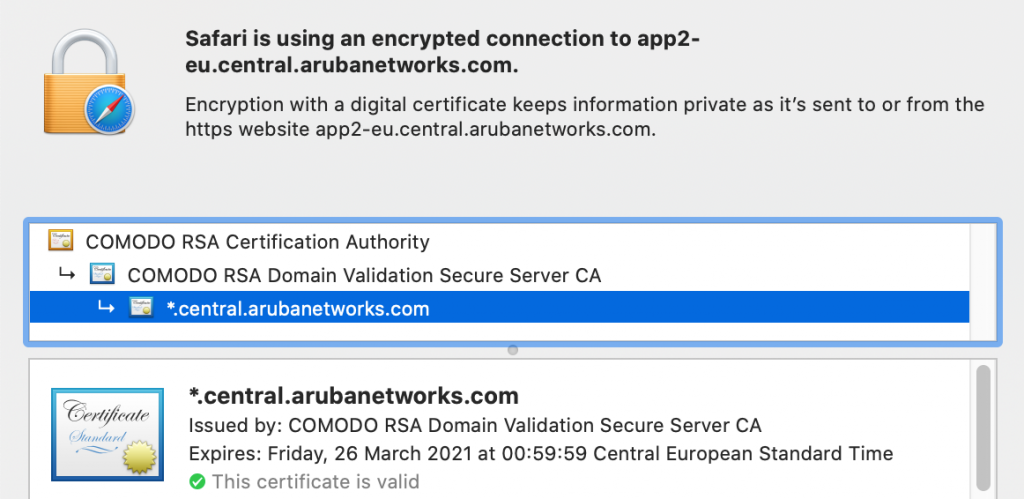
The COMODO RSA Certificate Authority certificate can be downloaded via the following link: https://support.comodo.com/index.php?/Knowledgebase/Article/View/969/108/root-comodo-rsa-certification-authority-sha-2
The link shows the certificate in PEM format, which can be used to add the PKI TA-Profile to the switch.
6200F(config)# crypto pki ta-profile COMODO_RSA_CA
6200F(config-ta-COMODO_CA)# ta-certificate import terminal
Paste the certificate in PEM format below, then hit enter and ctrl-D:
6200F(config-ta-cert)# —–BEGIN CERTIFICATE—–
6200F(config-ta-cert)# MIIF2DCCA8CgAwIBAgIQTKr5yttjb+Af907YWwOGnTANBgkqhkiG9w0BAQwFADCB
6200F(config-ta-cert)# hTELMAkGA1UEBhMCR0IxGzAZBgNVBAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4G
6200F(config-ta-cert)# A1UEBxMHU2FsZm9yZDEaMBgGA1UEChMRQ09NT0RPIENBIExpbWl0ZWQxKzApBgNV
6200F(config-ta-cert)# BAMTIkNPTU9ETyBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTAwMTE5
6200F(config-ta-cert)# MDAwMDAwWhcNMzgwMTE4MjM1OTU5WjCBhTELMAkGA1UEBhMCR0IxGzAZBgNVBAgT
6200F(config-ta-cert)# EkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4GA1UEBxMHU2FsZm9yZDEaMBgGA1UEChMR
6200F(config-ta-cert)# Q09NT0RPIENBIExpbWl0ZWQxKzApBgNVBAMTIkNPTU9ETyBSU0EgQ2VydGlmaWNh
6200F(config-ta-cert)# dGlvbiBBdXRob3JpdHkwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCR
6200F(config-ta-cert)# 6FSS0gpWsawNJN3Fz0RndJkrN6N9I3AAcbxT38T6KhKPS38QVr2fcHK3YX/JSw8X
6200F(config-ta-cert)# pz3jsARh7v8Rl8f0hj4K+j5c+ZPmNHrZFGvnnLOFoIJ6dq9xkNfs/Q36nGz637CC
6200F(config-ta-cert)# 9BR++b7Epi9Pf5l/tfxnQ3K9DADWietrLNPtj5gcFKt+5eNu/Nio5JIk2kNrYrhV
6200F(config-ta-cert)# /erBvGy2i/MOjZrkm2xpmfh4SDBF1a3hDTxFYPwyllEnvGfDyi62a+pGx8cgoLEf
6200F(config-ta-cert)# Zd5ICLqkTqnyg0Y3hOvozIFIQ2dOciqbXL1MGyiKXCJ7tKuY2e7gUYPDCUZObT6Z
6200F(config-ta-cert)# +pUX2nwzV0E8jVHtC7ZcryxjGt9XyD+86V3Em69FmeKjWiS0uqlWPc9vqv9JWL7w
6200F(config-ta-cert)# qP/0uK3pN/u6uPQLOvnoQ0IeidiEyxPx2bvhiWC4jChWrBQdnArncevPDt09qZah
6200F(config-ta-cert)# SL0896+1DSJMwBGB7FY79tOi4lu3sgQiUpWAk2nojkxl8ZEDLXB0AuqLZxUpaVIC
6200F(config-ta-cert)# u9ffUGpVRr+goyhhf3DQw6KqLCGqR84onAZFdr+CGCe01a60y1Dma/RMhnEw6abf
6200F(config-ta-cert)# Fobg2P9A3fvQQoh/ozM6LlweQRGBY84YcWsr7KaKtzFcOmpH4MN5WdYgGq/yapiq
6200F(config-ta-cert)# crxXStJLnbsQ/LBMQeXtHT1eKJ2czL+zUdqnR+WEUwIDAQABo0IwQDAdBgNVHQ4E
6200F(config-ta-cert)# FgQUu69+Aj36pvE8hI6t7jiY7NkyMtQwDgYDVR0PAQH/BAQDAgEGMA8GA1UdEwEB
6200F(config-ta-cert)# /wQFMAMBAf8wDQYJKoZIhvcNAQEMBQADggIBAArx1UaEt65Ru2yyTUEUAJNMnMvl
6200F(config-ta-cert)# wFTPoCWOAvn9sKIN9SCYPBMtrFaisNZ+EZLpLrqeLppysb0ZRGxhNaKatBYSaVqM
6200F(config-ta-cert)# 4dc+pBroLwP0rmEdEBsqpIt6xf4FpuHA1sj+nq6PK7o9mfjYcwlYRm6mnPTXJ9OV
6200F(config-ta-cert)# 2jeDchzTc+CiR5kDOF3VSXkAKRzH7JsgHAckaVd4sjn8OoSgtZx8jb8uk2Intzna
6200F(config-ta-cert)# FxiuvTwJaP+EmzzV1gsD41eeFPfR60/IvYcjt7ZJQ3mFXLrrkguhxuhoqEwWsRqZ
6200F(config-ta-cert)# CuhTLJK7oQkYdQxlqHvLI7cawiiFwxv/0Cti76R7CZGYZ4wUAc1oBmpjIXUDgIiK
6200F(config-ta-cert)# boHGhfKppC3n9KUkEEeDys30jXlYsQab5xoq2Z0B15R97QNKyvDb6KkBPvVWmcke
6200F(config-ta-cert)# jkk9u+UJueBPSZI9FoJAzMxZxuY67RIuaTxslbH9qh17f4a+Hg4yRvv7E491f0yL
6200F(config-ta-cert)# S0Zj/gA0QHDBw7mh3aZw4gSzQbzpgJHqZJx64SIDqZxubw5lT2yHh17zbqD5daWb
6200F(config-ta-cert)# QOhTsiedSrnAdyGN/4fy3ryM7xfft0kL0fJuMAsaDk527RH89elWsn2/x20Kk4yl
6200F(config-ta-cert)# 0MC2Hb46TpSi125sC8KKfPog88Tk5c0NqMuRkrF8hey1FGlmDoLnzc7ILaZRfyHB
6200F(config-ta-cert)# NVOFBkpdn627G190
6200F(config-ta-cert)# —–END CERTIFICATE—–
6200F(config-ta-cert)#
6200F(config-ta-cert)#
The certificate you are importing has the following attributes:
Subject: C = GB, ST = Greater Manchester, L = Salford, O = COMODO CA Limited, CN = COMODO RSA Certification Authority
Issuer: C = GB, ST = Greater Manchester, L = Salford, O = COMODO CA Limited, CN = COMODO RSA Certification Authority
Serial Number: 0x4CAAF9CADB636FE01FF74ED85B03869D
TA certificate import is allowed only once for a TA profile
Do you want to accept this certificate (y/n)? y
6200F(config-ta-COMODO_CA)#
The connection to Central is successful after adding the PKI TA-Profile for the COMODO certificate. You are now ready to get going with the template configuration for the AOS-CX switch in Aruba Central.
DON’T FORGET TO ADD THE CERTIFICATE TO THE TEMPLATE GROUP IN CENTRAL!
Of course you can always try to debug the Central connection with the commando’s
debug central all
debug destination buffer
show debug buffer reverse
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021