Configuration Example, Management
phpIPAM – Azure and SAML authentication
What is easier than using your Azure credentials to log in to your web applications like phpIPAM? My daily job is networking, like routing, switching, wireless, and Wi-Fi, so I had to puzzle when I had to configure SAML2 authentication between phpIPAM and our company Azure infrastructure. I couldn’t find a lot of information about the configuration, but I managed to get it done eventually.
The only thing that doesn’t seem to work is the mapping between a local user and the Azure user. Every successful authentication from Azure ends up by signing in with the default phpIPAM admin user. I can live with that (for now). To get the configuration done, you need to follow these steps:
- Access the Azure portal via https://portal.azure.com
- Navigate to Azure Active Directory
- Choose Enterprise Applications
- Configure a New Application
- Choose the option Non-gallery application
- Configure a name for the application and choose Add
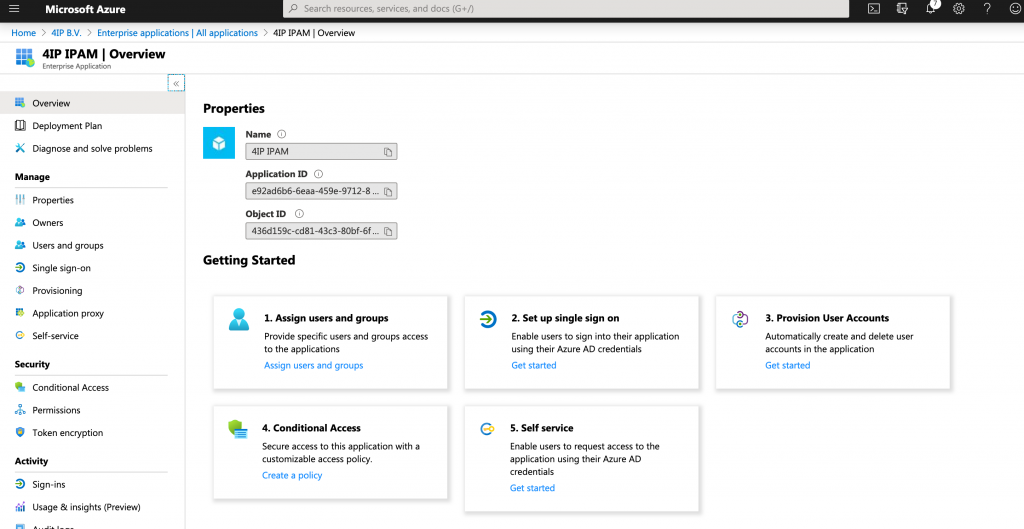
The next step is to configure the single sign on part of Azure.
- Choose option 2. Set up single sign on from the above image
- Edit the Basic SAML Configuration
- Enter the following information (our phpIPAM URL is https://ipam.4ip.nl)
- Identifier (Entity ID): https://ipam.4ip.nl
- Reply URL (Assertion Consumer Service URL): https://ipam.4ip.nl/saml2
- Save the configuration
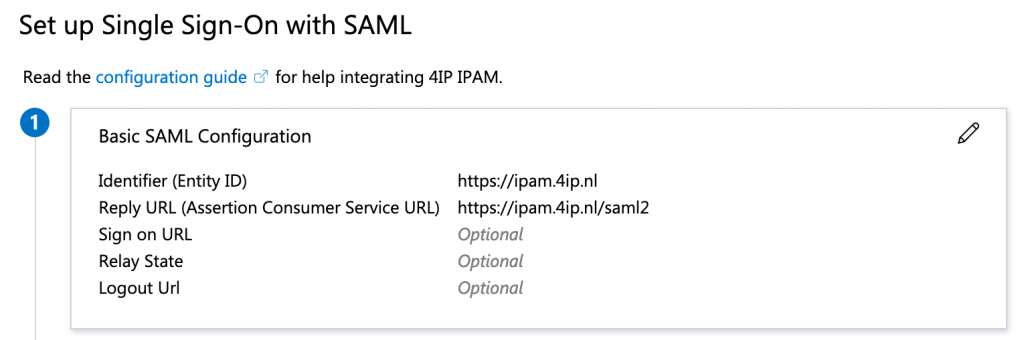
The next step involves downloading the SAML Signing Certificate and get the certificate fingerprint. You can download the certificate under 3 SAML Signing Certificate.
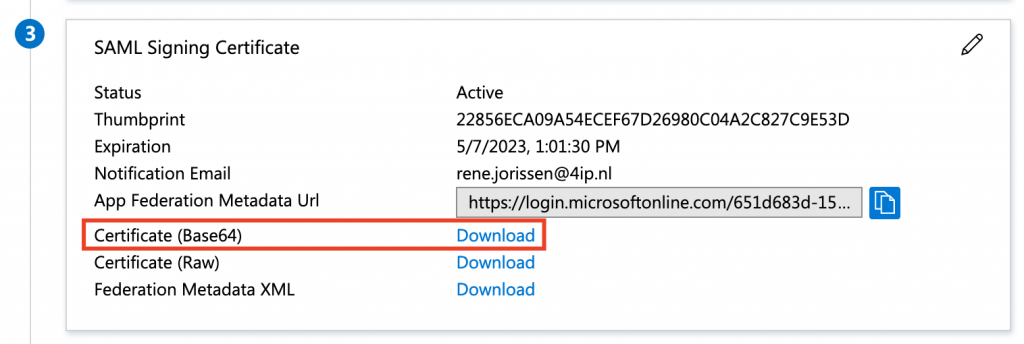
Download and save the Base64 certificate. I use OpenSSL and the following command to retrieve the fingerprint:
openssl x509 -in saml-cert.cer -fingerprint -sha256 -noout -text
You find the fingerprint at the end of the output. Save the fingerprint. The last piece of information is the links to Azure AD. Mine can be found below.
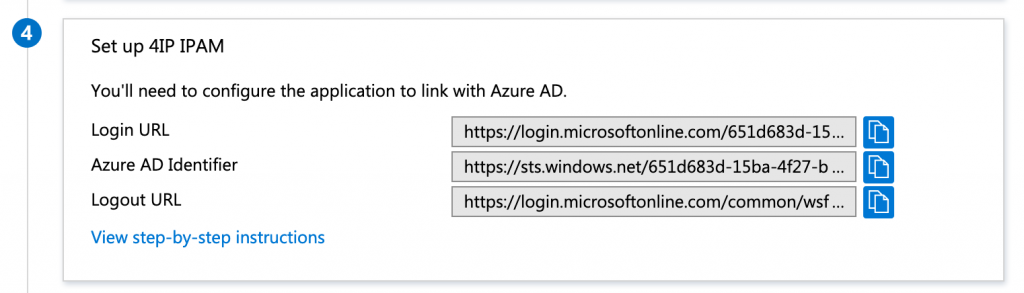
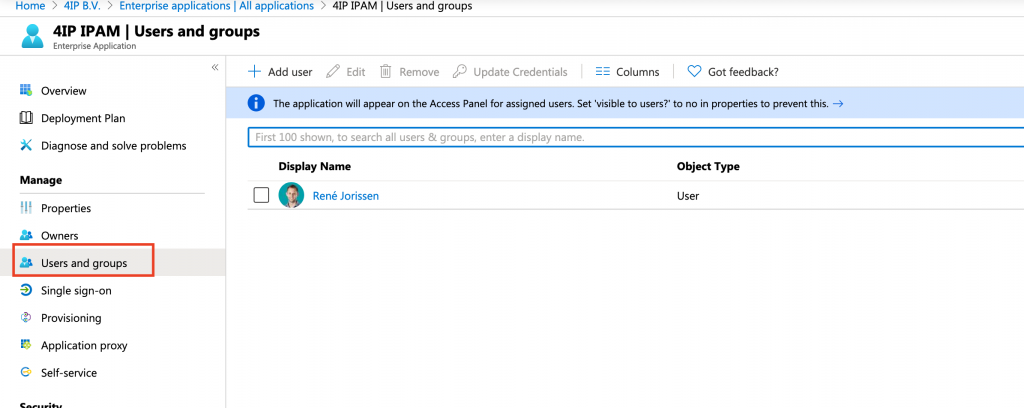
You have all the information to go ahead and configure the SAML connection in phpIPAM. The last step is to add users or groups to the Enterprise application. Choose Users and Groups from the menu and add the users or groups which are allowed to have access. We don’t have a premium subscription, so I can only add single users and no groups.
This is it for the Azure part. The next step is the phpIPAM configuration. Log in to your phpIPAM environment and go to the Authentication Methods in phpIPAM and create a new SAML2 Authentication. Enter all the information from the Azure portal into the correct fields.
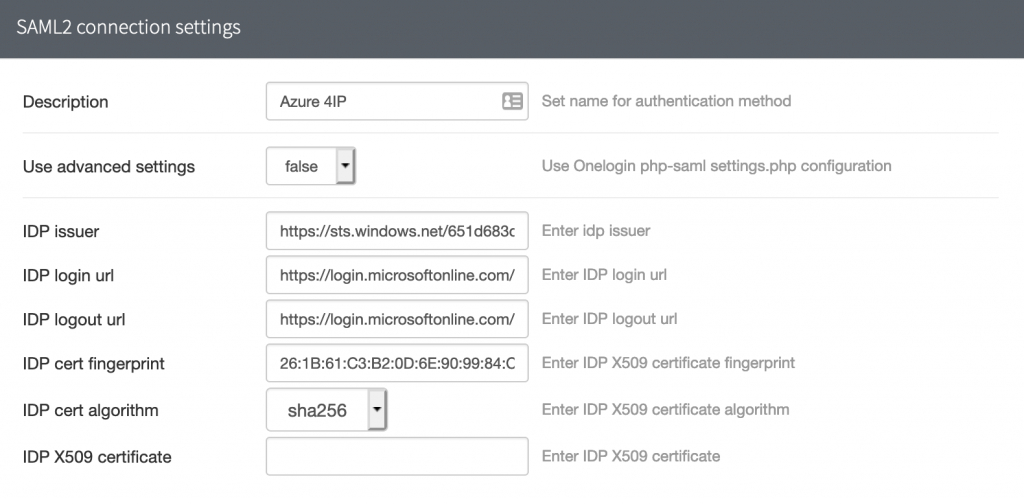
Use the following information.
| phpIPAM | Azure |
| IDP issuer | Azure AD Identifier |
| IDP login url | Login URL |
| IDP logout url | Logout URL |
| IDP cert fingerprint | Openssl fingerprint |
Add the SAML2 Authentication Method. The next step would be to create a local user in phpIPAM and associate the user with the SAML2 Authentication Method.
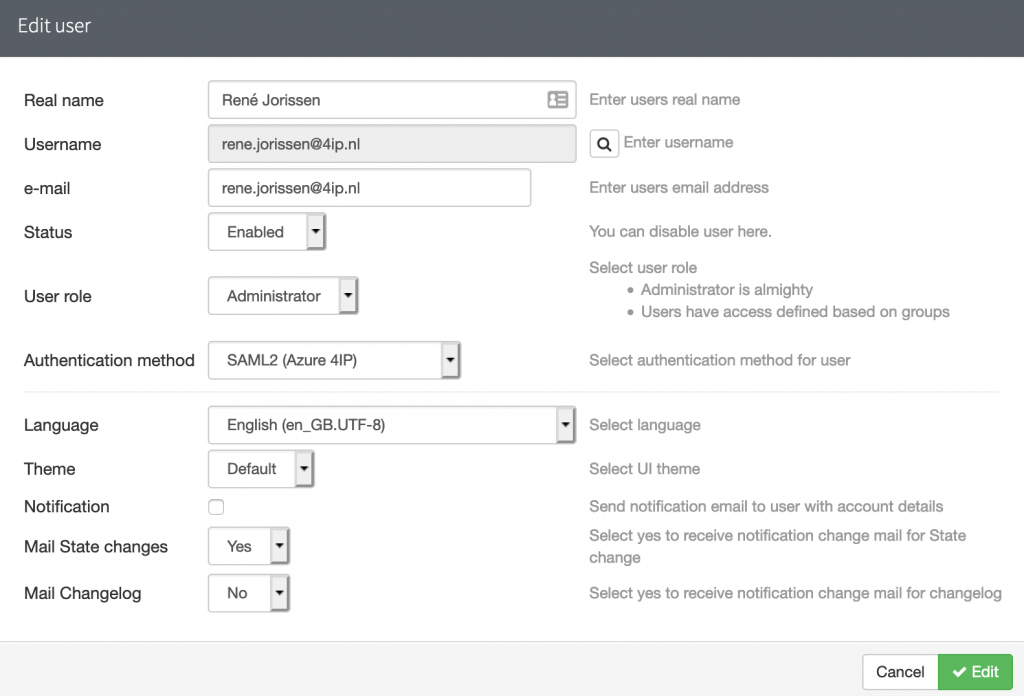
You are now ready to test your SAML integration. I now have the opportunity to log in with my Azure account, including MFA, to access the phpIPAM environment.
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021
User mapping solution found at https://ramblingcurtis.blogspot.com/2020/05/single-sign-on-for-phpipam-with-vmware.html:
Preventing all SAML authenticated users mapping to Admin
Returning to the Server’s terminal, we need to make a change to a file. Without this change, once SAML is set up, all users get mapped to Admin.
Using nano, we edit the config.php file:
sudo nano /var/etc/www/html/phpipam/config.php
Search for a line that begins “ define(‘MAP_SAML_USER’ ” and change the value from true to false.
eEasy peasy with your guidance,
Thanks,
you are the bomb