Configuration Example, Management
RADIUS Authentication
I am sure that many of you would like to do the same thing and many of you successfully configured it. I am trying to configure RADIUS Authentication on my Cisco 877W. I have two different RADIUS policies, the first for privilege level 1 and the second for privilege level 15. I am using Microsoft IAS as RADIUS server.
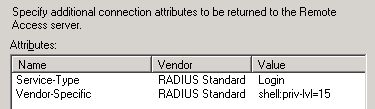
I configured two policies and the second policy has the following Advanced Options set.
This means that the user should get privilege level 15, when logging in. I configured the following on the Cisco877W router.
aaa authentication login AD group radius local none
aaa authorization exec AD group radius
!
radius-server host 10.10.1.1 auth-port 1812 acct-port 1813 key 7 KEY
radius-server retry method reorder
radius-server transaction max-tries 2
radius-server timeout 4
radius-server deadtime 2
radius-server vsa send authentication
!
line vty 0 4
session-timeout 5
access-class 10 in
exec-timeout 5 0
login authentication AD
transport preferred none
transport input ssh
transport output telnet ssh
The user doesn’t get the privilege level 15, but comes in privilege level 1 and has to enter enable to get into privilege level 15. I turned on RADIUS debugging and I see the shell code coming by, as the debug output below shows.
%SSH-5-SSH2_SESSION: SSH2 Session request from 10.10.1.103 (tty = 1)
using crypto cipher ‘aes256-cbc’, hmac ‘hmac-sha1’ Succeeded
RADIUS/ENCODE(00000716): ask “Password: ”
RADIUS/ENCODE(00000716): send packet; GET_PASSWORD
RADIUS/ENCODE(00000716):Orig. component type = EXEC
RADIUS/ENCODE(00000716): dropping service type,
“radius-server attribute 6 on-for-login-auth” is off
RADIUS(00000716): Config NAS IP: 0.0.0.0
RADIUS/ENCODE(00000716): acct_session_id: 1814
RADIUS(00000716): sending
RADIUS/ENCODE: Best Local IP-Address 10.10.1.1 for Radius-Server 10.10.1.5
RADIUS(00000716): Send Access-Request to 10.10.1.5:1812 id 1645/31, len 81
RADIUS: authenticator 72 D9 B5 F1 76 72 9A D1 – 73 D7 E8 AF 21 F3 B5 0F
RADIUS: User-Name [1] 6 “rene”
RADIUS: User-Password [2] 18 *
RADIUS: NAS-Port [5] 6 3
RADIUS: NAS-Port-Id [87] 6 “tty3”
RADIUS: NAS-Port-Type [61] 6 Virtual [5]
RADIUS: Calling-Station-Id [31] 13 “10.10.1.103”
RADIUS: NAS-IP-Address [4] 6 10.10.1.1
RADIUS: Received from id 1645/31 10.10.1.5:1812, Access-Accept, len 83
RADIUS: authenticator BB BF B5 FD 1D 36 67 9B – FE 5A EE 5A 6C 42 5E B9
RADIUS: Vendor, Cisco [26] 25
RADIUS: Cisco AVpair [1]
19 “shell:priv-lvl=15”
RADIUS: Service-Type [6]
6 Login [1]
RADIUS: Class [25] 32
RADIUS: 3C 09 04 AE 00 00 01 37
00 01 0A 0A 01 05 01 C8 [< ??????7????????]
RADIUS: A6 C0 C2 0D FD 4C 00
00 00 00 00 00 00 13 [?????L????????]
RADIUS(00000716): Received from id 1645/31
%SEC_LOGIN-5-LOGIN_SUCCESS: Login Success
[user: rene] [Source: 10.10.1.103] [localport: 22]
I am running out of options. I have tried to use the Cisco-AVpair in IAS, but no success. I tried using only Telnet, but no success. Maybe someone has an option to try…
René Jorissen
Latest posts by René Jorissen (see all)
- MacOS Big Sur and SSLKEYFILELOG - November 23, 2021
- ClearPass, Azure AD, SSO and Object ID - August 12, 2021
- ClearPass – custom MPSK - July 20, 2021
radius-server vsa send authentication
This command limits vendor specific commands to authentication only, rather than authorization. I think that may be why the AV pair for level 15 is being ignored.